Using Shodan as a tool to find vulnerable devices | GRI Blog
In the last blog post, we looked at the case study of the Kemuri Water company as outlined by the Verizon Data Breach Report which underscored potential consequences of having industrial control systems connected to the public internet. This post will go a little bit deeper and look at the ease in which a device similar to those that were probably in use at the water company and connected to the public internet can be found and potentially exploited.
For this process I used the tool ‘Shodan’. Shodan is essentially a search engine for internet connected devices. It ‘crawls’ the internet, sending out connection requests and recording the public results, which include banner information, open ports, and running services. There have been numerous articles and blogs that highlight how Shodan has been used to find devices that are part of the ‘internet of things,’ such as webcameras, license plate readers, programmable logic controllers (PLC), even ships using satellite antennas and botnet command and control servers.
Let’s look at an example. Using a search function in Shodan that looks for Siemens S7 PLCs, placing the results on a map and looking in the northeastern United States, we find this result which appears to be a PLC in the Newark, New Jersey area.
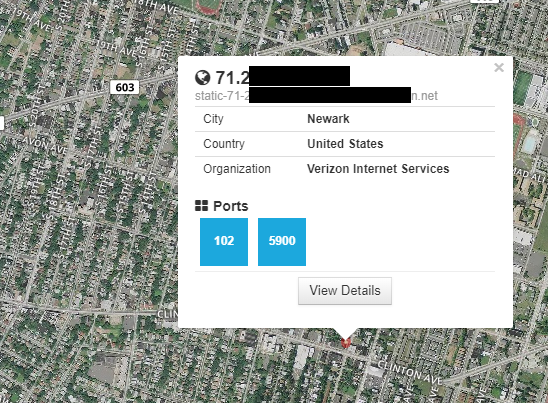
Looking at the Shodan details we can see the services running. Port 102 is a proprietary port used by Siemens devices for communication via TCP and port 5900 is open and running a VNC/HTTP server which is used for outside remote access to the PLC’s settings. There is some important banner info here too. Looking at the port 102 banner there are specific details on the Hardware/Module/Firmware. A quick search on Siemens website for the module reveals that this PLC is a SIMATIC S7-1200. Further examination reveals that this product has already been announced as being phased out in 2014, is no longer offered for sale and is only supported until 2022 for parts. A look into the technical data reveals that this PLC is only capable of running Firmware Version 3 for Siemens and not the newest Version 4. This leads us to the next site of interest which is at the Department of Homeland Security ICS-CERT website.
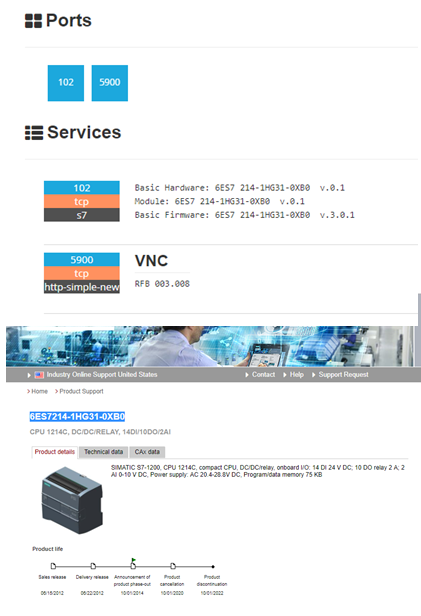 A quick lookup of this model (Siemens S7-1200) reveals that in March of 2014, six months before the product was discontinued and scheduled for phase out, Advisory ICSA-14-079-02 was issued. The advisory outlines six vulnerabilities in the S7-1200, most notably for our example is CVE-2014-2256 which outlines that “an attacker could cause the device to go into defect mode if specially crafted packets are sent to port 102/TCP” causing a denial of service attack. Port 102 is open and was found as part of our Shodan results. The mitigation for all six CVE’s is to install Firmware Version 4 on the PLC. Unfortunately for the module we found, as noted above, Version 4 is not able to be upgraded to and as we saw in the Shodan results, this PLC is currently running Version 3. Therefore this PLC is vulnerable. Knowing the IP and the potential vulnerabilities, an attacker could run targeted scans and attempt to connect and send crafted packets to the PLC which could result in denial of service or exploitation of the other CVE’s could lead to potential device control.
A quick lookup of this model (Siemens S7-1200) reveals that in March of 2014, six months before the product was discontinued and scheduled for phase out, Advisory ICSA-14-079-02 was issued. The advisory outlines six vulnerabilities in the S7-1200, most notably for our example is CVE-2014-2256 which outlines that “an attacker could cause the device to go into defect mode if specially crafted packets are sent to port 102/TCP” causing a denial of service attack. Port 102 is open and was found as part of our Shodan results. The mitigation for all six CVE’s is to install Firmware Version 4 on the PLC. Unfortunately for the module we found, as noted above, Version 4 is not able to be upgraded to and as we saw in the Shodan results, this PLC is currently running Version 3. Therefore this PLC is vulnerable. Knowing the IP and the potential vulnerabilities, an attacker could run targeted scans and attempt to connect and send crafted packets to the PLC which could result in denial of service or exploitation of the other CVE’s could lead to potential device control.
There are a few major unknowns in this example. First, it is unclear what the PLC is being used for. The pin on the Shodan map is an abandoned building in Newark on Google Maps. The description of the PLC on ICS-CERT describes it as being used for “discrete and continuous control in industrial environments such as manufacturing, food and beverages, and chemical industries worldwide”. Second, we do not know who the owner is. The PLC is connected using Verizon Internet and Verizon is returned as the owner of the IP address upon conducting a domain name service query. A further step could be to contact Verizon and alert them to that specific IP address and relay the findings above. They could then take further action to secure the device or notify its operator. The Department of Homeland Security run ICS-CERT has already published its advisory on the device, Siemens has released updated firmware, and without knowing what process the PLC is controlling, the owner may not be under a legal responsibility to update or replace it with a newer model. At the end of the day though, this PLC was one of over 125 Siemens PLCs that were found using Shodan to be publicly discoverable, is in an urban area, most likely controls an industrial process, and is discoverable on the public internet and vulnerable.
